Understanding your risk
As a small business, you are a prime target for data thieves.
When your payment card data is breached, the fallout can strike quickly. Your customers lose trust in your ability to protect their personal information. They take their business elsewhere. There are potential financial penalties and damages from lawsuits, and your business may lose the ability to accept payment cards. A survey of 1,015 small and medium businesses found 60% of those breached close in six months. (NCSA)
What’s at risk?
YOUR CUSTOMERS’ CARD DATA IS A GOLD MINE FOR CRIMINALS. DON’T LET THIS HAPPEN TO YOU!
Follow the actions in this guide to protect against data theft.
Examples of payment card data are the primary account number (PAN) and three or four-digit card security code. The red arrows below point to types of data that require protection.
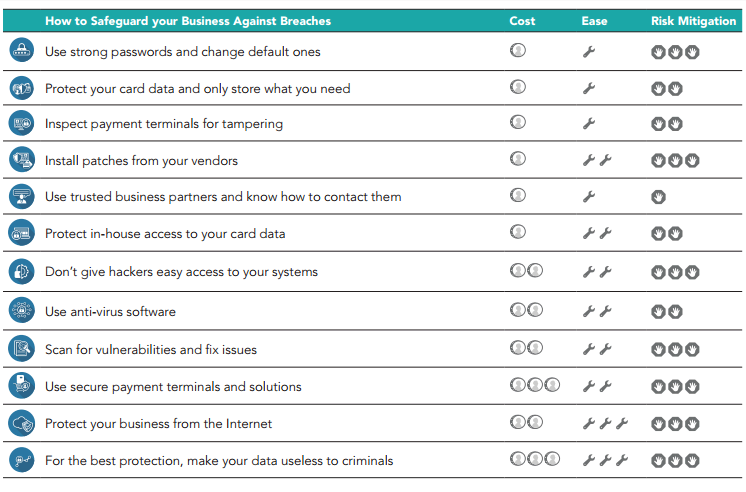
Understanding your payment system: Common payment terms
Depending on where in the world you are located, equipment used to take payments is called by different names. Here are the types we reference in this document and what they are commonly called.
A PAYMENT TERMINAL is the device used to take customer card payments via swipe, dip, insert, tap, or manual entry of the card number. Point-of-sale (or POS) terminal, credit card machine, PDQ terminal, or EMV/chip-enabled terminal are also names used to
describe these devices.
An ELECTRONIC CASH REGISTER (or till) registers and calculates transactions, and may print out receipts, but it does not accept customer card payments.
An INTEGRATED PAYMENT TERMINAL is a payment terminal and electronic cash register in one, meaning it takes card payments,
registers and calculates transactions, and prints receipts.
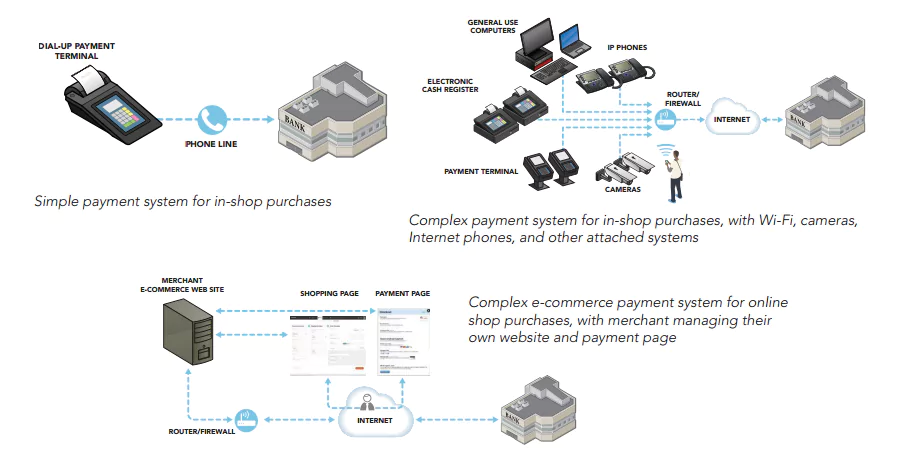
A PAYMENT SYSTEM encompasses the entire process of accepting card payments in a retail location (including stores/shops and e-commerce storefronts), and may include a payment terminal, an electronic cash register, other devices or systems connected to a
payment terminal (for example, Wi-Fi for connectivity or a PC used for inventory), servers with e-commerce components such as payment pages, and the connections out to the merchant bank.
A MERCHANT BANK is a bank or a financial institution that processes credit and/or debit card payments on behalf of merchants. Acquirer, acquiring bank, and card or payment processor are also terms for this entity.
How is your business at risk?
The more features your payment system has, the more complex it is to secure. These extra features often provide easy ways for criminals to steal your customer card data. Think carefully about whether you really need these extra features (for example, Wi-Fi or cameras) for your business.
How do you sell your goods or services? There are three main ways:
1. A person walks into your shop and makes a purchase with their card.
2. A person visits your website and pays online.
3. A person calls your shop and provides card details over the phone, or sends the details in the mail or via fax.
Understanding your risk: Payment system types
Your security risks vary greatly depending on the complexity of your payment system, whether face-to-face or online.
can start protecting your business today with these security basics:
Use strong passwords and change default ones
Your passwords are vital for computer and card data security. Just like a lock on your door protects physical property, a password helps
protect your business data. Also be aware that computer equipment and software out of the box (including your payment terminal) often
come with default (preset) passwords such as “password” or “admin,” which are commonly known by hackers and are a frequent source of small merchant breaches.
CHANGE YOUR PASSWORDS REGULARLY. Treat your passwords like a toothbrush. Don’t let anyone else use them and get new ones every three months.
SEEK HELP. Ask your vendors or service providers about default passwords and how to change them. Then do it!
MAKE THEM HARD TO GUESS. The most common passwords are “password” and “123456.” Hackers try easily-guessed passwords because they’re used by half of all people. A strong password has seven or more characters and a combination of upper and lower case letters, numbers, and symbols (like !@#$&*). A phrase can also be a strong password (and may be easier to remember), like “B1gMac&frieS.”
DON’T SHARE. Insist on each employee having their own login IDs and passwords – never share!
Protect card data and only store what you need
It’s impossible to protect card data if you don’t know where it is.
What can you do?
ASK AN EXPERT. Ask your payment terminal vendor or merchant bank where your systems store data and if you can simplify how you process payments. Also ask how to conduct specific transactions (for example, for recurring payments) without storing the card’s security code.
OUTSOURCE. The best way to protect against data breaches is not to store card data at all. Consider outsourcing your card processing to a PCI DSS compliant service provider.
IF YOU DON’T NEED CARD DATA, DON’T STORE IT. Securely destroy/shred card data you don’t need. If you need to keep paper with sensitive card data, mark through the data with a thick, black marker until it is unreadable and secure the paper in a locked drawer or safe that only a few people have access to.
LIMIT RISK. Rather than accepting payment details via email, ask customers to provide it via phone, fax, or regular mail.
TOKENIZE OR ENCRYPT. Ask your merchant bank if you REALLY need to store that card data. If you do, ask your merchant bank or service provider about encryption or tokenization technologies that make card data useless even if stolen.